Corporate surveillance
| Business administration |
|---|
| Management of a business |
Corporate surveillance describes the practice of businesses monitoring and extracting information from their users, clients, or staff.[1] This information may consist of online browsing history, email correspondence, phone calls, location data, and other private details. Acts of corporate surveillance frequently look to boost results, detect potential security problems, or adjust advertising strategies. These practices have been criticized for violating ethical standards and invading personal privacy. Critics and privacy activists have called for businesses to incorporate rules and transparency surrounding their monitoring methods to ensure they are not misusing their position of authority or breaching regulatory standards.[2]
Monitoring can feel intrusive and give the impression that the business does not promote ethical behavior among its personnel. Staff satisfaction, productivity, and staff turnover may all suffer as a result of the invasion of privacy.[3]
Monitoring methods
Employers may be authorized to gather information through keystroke logging and mouse tracking, which involves recording the keys individuals interact with and cursor position on computers. In cases where employment contracts permit it, they may also monitor webcam activity on company-provided computers. Employers may be able to view the emails sent from business accounts and may be able to see the websites visited when using a corporate internet connection.[4] The screenshot capability is another tool that enables companies to see what remote workers are doing. This feature, which can be found in tracking software, takes screenshots throughout the day at predetermined or arbitrary intervals.[5] Additionally, people who don't work in offices are observed. For instance, it has been claimed that Amazon has incorporated tracking technology to monitor warehouse staff and delivery drivers.[4]
Use of collected information
Information collected by corporations can be used for a variety of uses including marketing research, targeting advertising, fraud detection and prevention, ensuring policy adherence, preventing lawsuits, and safeguarding records and company assets.[6]
Privacy concerns
Concerns over corporate privacy have become more important due to companies collection and manipulation of personal data.[7] Since these practices have been recognized there has been a rising concern about both the security and the possible mishandling of the data accumulated.
Social Media data collection and monitoring has been one of the most concerned areas regarding corporate surveillance. Recently, many employers on CareerBuilder have checked their potential candidates' social media activities before the hiring process.[8] This approach can be excusable since it is important to be aware of a future employee or applicant's online presence, and how it might affect the company's reputation in the future. This is crucial since employers are often made legally responsible for their worker's digital actions.[9]
These data can also be used to enact political gains. The Facebook-Cambridge Analytica data scandal in 2018 revealed that its British branch to have surreptitiously sold American psychological data to the Trump campaign.[10] This information was supposed to be private, but Facebook's inability to protect user information had reportedly not been a top priority of the company at the time.[11]
Laws and regulations
- The National Labor and Relations Act (NLRA) safeguards workplace democracy by giving workers in the private sector the basic freedom to demand better working conditions and choice of representation without fear of retaliation.[12]
- General Data Protection Regulation (GDPR) outlines the broad responsibilities of data controllers and the "processors" that handle personal data on their behalf. They must adopt the necessary security measures in accordance with the risk involved in the data processing operations they carry out.[1]
- Electronics Communication Privacy Act (ECPA), as amended, provides protection for electronic, oral, and wire communications while they are being created, while they are being sent, and while they are being stored on computers. Email, phone calls, and electronically stored data are covered by the Act.[13]
Sale of customer data
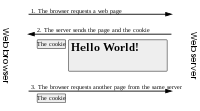

If it is business intelligence, data collected on individuals and groups can be sold to other corporations, so that they can use it for the aforementioned purpose. It can be used for direct marketing purposes, such as targeted advertisements on Google and Yahoo. These ads are tailored to the individual user of the search engine by analyzing their search history and emails[14] (if they use free webmail services).
For example, the world's most popular web search engine stores identifying information for each web search. Google stores an IP address and the search phrase used in a database for up to 2 years.[15] Google also scans the content of emails of users of its Gmail webmail service, in order to create targeted advertising based on what people are talking about in their personal email correspondences.[16] Google is, by far, the largest web advertising agency. Their revenue model is based on receiving payments from advertisers for each page-visit resulting from a visitor clicking on a Google AdWords ad, hosted either on a Google service or a third-party website. Millions of sites place Google's advertising banners and links on their websites, in order to share this profit from visitors who click on the ads. Each page containing Google advertisements adds, reads, and modifies cookies on each visitor's computer.[17] These cookies track the user across all of these sites, and gather information about their web surfing habits, keeping track of which sites they visit, and what they do when they are on these sites. This information, along with the information from their email accounts, and search engine histories, is stored by Google to use for building a profile of the user to deliver better-targeted advertising.[16]
Surveillance of workers

In 1993, David Steingard and Dale Fitzgibbons argued that modern management, far from empowering workers, had features of neo-Taylorism, where teamwork perpetuated surveillance and control. They argued that employees had become their own "thought police" and the team gaze was the equivalent of Bentham's panopticon guard tower.[18] A critical evaluation of the Hawthorne Plant experiments has in turn given rise to the notion of a Hawthorne effect, where workers increase their productivity in response to their awareness of being observed or because they are gratified for being chosen to participate in a project.[19]
According to the American Management Association and the ePolicy Institute, who undertook a quantitative survey in 2007 about electronic monitoring and surveillance with approximately 300 US companies, "more than one fourth of employers have fired workers for misusing email and nearly one third have fired employees for misusing the Internet."[20] Furthermore, about 30 percent of the companies had also fired employees for usage of "inappropriate or offensive language" and "viewing, downloading, or uploading inappropriate/offensive content."[20] More than 40 percent of the companies monitor email traffic of their workers, and 66 percent of corporations monitor Internet connections.[20] In addition, most companies use software to block websites such as sites with games, social networking, entertainment, shopping, and sports. The American Management Association and the ePolicy Institute also stress that companies track content that is being written about them, for example by monitoring blogs and social media, and scanning all files that are stored in a filesystem.[20]
Government use of corporate surveillance data
The United States government often gains access to corporate databases, either by producing a warrant for it, or by asking. The Department of Homeland Security has openly stated that it uses data collected from consumer credit and direct marketing agencies—such as Google—for augmenting the profiles of individuals that it is monitoring.[21] The US government has gathered information from grocery store discount card programs, which track customers' shopping patterns and store them in databases, in order to look for terrorists by analyzing shoppers' buying patterns.[22]
Corporate surveillance of citizens
According to Dennis Broeders, "Big Brother is joined by big business".[23] He argues that corporations are in any event interested in data on their potential customers and that placing some forms of surveillance in the hands of companies, results in companies owning video surveillance data for stores and public places. The commercial availability of surveillance systems has led to their rapid spread. Therefore it is almost impossible for citizens to maintain their anonymity.[23]
When businesses can monitor their customers, such customers run the risk of facing prejudice when applying for housing, loans, jobs, and other economic opportunities.[24] The consumer may not even be aware that they are being treated differently if discrimination results in different prices being charged for the same goods. Without their knowledge, their information was being accessed and sold.
In February 2024, concerns over the collection of customer data without their knowledge were raised at the University of Waterloo following a post on Reddit and a published article in the school newspaper mathNEWS, in which vending machines displayed an error suggesting facial recognition software was in use by the machines. Following this error, the university requested for the machines to have their facial recognition software disabled and eventually removed.[25][26] On February 29, the Ontario privacy commissioner announced that it would be beginning an investigation into the installation of the vending machines.[27]
See also
- Big data
- Computer surveillance in the workplace
- Employee monitoring
- Keystroke logging
- Loyalty program
- Mouse tracking
- Shopping cart software
- Surveillance capitalism
References
- ^ Wagner, Isabel (2022-03-24). Auditing Corporate Surveillance Systems. Cambridge University Press. doi:10.1017/9781108946940. ISBN 978-1-108-94694-0. S2CID 247687128.
- ^ "Social Media Surveillance by the U.S. Government | Brennan Center for Justice". www.brennancenter.org. Retrieved 2023-05-10.
- ^ "Laws and Ethics of Employment Monitoring and Privacy". Business News Daily. Retrieved 2023-04-26.
- ^ a b "Here are all the ways your boss can legally monitor you". Washington Post. ISSN 0190-8286. Retrieved 2023-05-01.
- ^ Czerwonka, Eric. "How do companies track employees? - Buddy Punch". buddypunch.com. Retrieved 2023-05-01.
- ^ "Corporate Surveillance".
- ^ Whitney, Lance (2021-08-17). "Data privacy is a growing concern for more consumers". TechRepublic. Retrieved 2023-05-10.
- ^ "Why Monitoring Employees' Social Media Is a Bad Idea". Time. 2015-05-22. Retrieved 2023-05-03.
- ^ "Why Monitoring Employees' Social Media Is a Bad Idea". Time. 2015-05-22. Retrieved 2023-05-03.
- ^ Confessore, Nicholas (2018-04-04). "Cambridge Analytica and Facebook: The Scandal and the Fallout So Far". The New York Times. ISSN 0362-4331. Retrieved 2023-05-08.
- ^ Confessore, Nicholas (2018-04-04). "Cambridge Analytica and Facebook: The Scandal and the Fallout So Far". The New York Times. ISSN 0362-4331. Retrieved 2023-05-08.
- ^ "National Labor Relations Act | National Labor Relations Board". www.nlrb.gov. Retrieved 2023-05-08.
- ^ "Electronic Communications Privacy Act of 1986 (ECPA)". Bureau of Justice Assistance. Retrieved 2023-05-08.
- ^ Louise Story (1 November 2007). "F.T.C. to Review Online Ads and Privacy". New York Times.
- ^ "Google privacy booklet" (PDF). Archived (PDF) from the original on 2020-10-21.
- ^ a b Priyanki Joshi (21 March 2009). "Every move you make, Google will be watching you". Business Standard.
- ^ "Advertising and Privacy". 2009. Retrieved 21 March 2009.
- ^ Jim Grieves (2003). Strategic Human Resource Development. SAGE. p. 58. ISBN 9781412932288.
- ^ Carl E. Van Horn; Herbert A. Schaffner, eds. (2003). Work in America: N-Z. ABC-CLIO. p. 245. ISBN 9781576076767.
- ^ a b c d American Management Association and the ePolicy Institute (2008). Electronic Monitoring and Surveillance 2007 Survey Archived 2012-08-01 at the Wayback Machine.
- ^ David von Drehle. "The Surveillance Society". Time.
- ^ Kelley Vlahos (1 August 2002). "Store Customer Cards a Source for FBI?". FOX News.
- ^ a b Dennis Broeders (2009). Breaking Down Anonymity: Digital Surveillance of Irregular Migrants in Germany and the Netherlands. Amsterdam University Press. p. 45. ISBN 9789089641595.
- ^ "Factsheet: Surveillance Advertising: Good for Consumers or the Ad-Tech Industry? · Consumer Federation of America". Consumer Federation of America. 26 August 2021. Retrieved 2023-05-03.
- ^ Stanley, River (molasses) (2024-02-16). "The M&M'S Machines are Watching You" (PDF). ISSN 0705-0410. Retrieved 2024-03-01.
- ^ Wiens, Colton (2024-02-22). "'Facial recognition' error message on vending machine sparks concern at University of Waterloo". ISSN 1494-8184. Retrieved 2024-03-01.
- ^ Baig, Fakiha (2024-03-01). "Complaints filed with Ontario's privacy commissioner over vending machines at University of Waterloo". Retrieved 2024-03-01.
